 What is
a Zone?
What is
a Zone?  What is
a Zone?
What is
a Zone? Zones are how ZoneAlarm Pro keeps track of the good, the bad, and the unknown out on the Internet.
Zones are virtual spaces—ways of classifying the computers and networks that your computer communicates with.
ZoneAlarm Pro looks at the Zone it is in—that is, whether it is good, bad, or unknown—to help decide what to do.
![]() Tip
To learn how to put a computer or network in the Trusted Zone, see the related
topic Adding to the Trusted Zone.
Tip
To learn how to put a computer or network in the Trusted Zone, see the related
topic Adding to the Trusted Zone.
 |
By default, ZoneAlarm Pro applies High security to the Internet Zone and Medium security to the Trusted Zone. You are safe from hackers out on the Internet, but you can share resources with the computers and networks you trust. No security level is necessary for the Blocked Zone, because NO traffic to or from that Zone is allowed. Using controls in the Firewall panel, you can adjust the security level for each Zone. |
 |
Tip Advanced users can customize high and medium security for each Zone by blocking or opening specific ports. For more information, see the related topic Blocking and unblocking ports. |
For more information on security levels, see the related topic Security levels.
Whenever a program wants access permission or server permission, ZoneAlarm Pro checks in the programs list. Each program has the following permission settings:
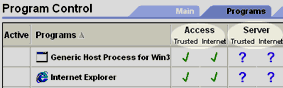
• Access permission for the Trusted Zone/Internet Zone
• Server permission for the Trusted Zone/Internet Zone
As you use your computer, ZoneAlarm Pro will display a New Program alert whenever a new program wants access or server permission.
To find out how to change access and server permissions for a program, see the related topic Changing program permissions.
Adding to the Trusted Zone
Blocking and unblocking ports
Changing program permissions
Zones tab
Trusted Zone tab
Security levels
access permission
Access permission allows a program on your computer to initiate communications
with another computer. This is distinct from server permission, which allows
a program to "listen" for connection requests from other computers.
You can give a program access permission for the Trusted Zone, the Internet
Zone, or both.
Several common applications may need access permission to operate normally. For example, your browser needs access permission in order to contact your ISP's servers. Your e-mail client (for example, MS Outlook) needs access permission in order to send or receive e-mail.
The following basic options are available for each program:
Allow
the program to connect to computers in the Internet Zone / Trusted Zone
Block the program from accessing computers in the Internet Zone / Trusted
Zone
Ask whether the program should have access permission (show Repeat
Program alert)
server permission
Server permission allows a program on your computer to "listen" for
connection requests from other computers, in effect giving those computers the
power to initiate communications with yours. This is distinct from access permission,
which allows a program to initiate a communications session with another computer.
Several common types of applications, such as chat programs, e-mail clients, and Internet Call Waiting programs, may need server permission to operate properly. Grant server permission only to programs you're sure you trust, and that require it in order to work.
If possible, avoid granting a program server permission for the Internet Zone. If you need to accept incoming connections from only a small number of machines, add those machines to the Trusted Zone, and then allow the program server permission for the Trusted Zone only.
The following basic options are available for each program
Allow
the program to listen for connection requests
Block the program from listening for connection requests
Ask me whether to allow the program to listen for connection requests
(show Server Program alert)